During the competition there are a few commands that will help you as much as the netstat command. “Netstat” stands for network status, and displays all the connections or listing connections on the system. While this command can be extremely powerful, the output to the untrained eye is very confusing. Not to mention all the command options that are available. For this reason we are going to only talk about one command on this blog post. Netstat is available on most operating systems (all that are part of the competition), however all the options are not the same. So I will introduce the tools using Microsoft Windows and end the post with Ubuntu.
What to Look for?
Regardless of using Windows or Linux you will need to understand what to look for when looking at netstat results. There are 3 primary groups of the TCP ports, they are: well-known ports, registered ports, and dynamic ports. More details on TCP ports can be researched on this Wikipedia page.
- Well-known ports – The port numbers in the range from 0 to 1023 are the well-known ports or system ports. They are used by system processes that provide widely used types of network services. On Unix-like operating systems, a process must execute with superuser privileges to be able to bind a network socket to an IP address using one of the well-known ports.
- Registered ports – The range of port numbers from 1024 to 49151 are the registered ports. They are assigned by IANA for specific service upon application by a requesting entity. On most systems, registered ports can be used without superuser privileges.
- Dynamic, private or ephemeral ports – The range 49152–65535 contains dynamic or private ports that cannot be registered with IANA. This range is used for private or customized services, for temporary purposes, and for automatic allocation of ephemeral ports.
This general definition should really be enough to get you started in understanding which open ports could be flags in the competition. However be careful, hackers often setup back doors on well-known ports in hopes that they can hide in plain site. There was an old saying, “if a it walks like a duck, and quacks like a duck, its not a goose.” Hackers often to try to disguise a goose to look like a duck. For example, they might setup a backdoor service to run on TCP port 80, which is used for web servers. Then as the administrator looks at the running port, and sees port 80 open and then ignores the port. If you see port 80 open and you know there is not a web server installed, then please investigate.
Netstat Output
The netstat command has several columns of output, the most important columns are:
- Local Address: displays the local socket (address and port) where the system is communicating.
- Foreign Address: displays the remote socket. If the socket is “0.0.0.0:0” then the port is an open service waiting for new connection.
- State: The state is the current status on the connection, see the chart below for detailed answers.
Netstat State Defined
- CLOSED: Indicates that the server has received an ACK signal from the client and the connection is closed
- CLOSE_WAIT: Indicates that the server has received the first FIN signal from the client and the connection is in the process of being closed
- ESTABLISHED: Indicates that the server received the SYN signal from the client and the session is established
- FIN_WAIT_1: Indicates that the connection is still active but not currently being used
- FIN_WAIT_2: Indicates that the client just received acknowledgment of the first FIN signal from the server
- LAST_ACK: Indicates that the server is in the process of sending its own FIN signal
- LISTENING: Indicates that the server is ready to accept a connection
- SYN_RECEIVED: Indicates that the server just received a SYN signal from the client
- SYN_SEND: Indicates that this particular connection is open and active
- TIME_WAIT: Indicates that the client recognizes the connection as still active but not currently being used
How to Use the Command
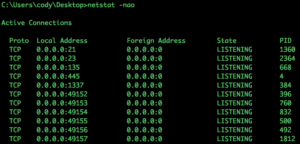
Now that you understand what to look for in the command and what some of the columns mean, lets look at the usage, again this is Windows usage. As with most command in Windows if you put the “/?” after the command you will get a list of helpful options to give the command. If you run the netstat command alone, a relatively simple list of all active TCP connections will be displayed.
This command is not useful for the competition, as the we are looking for backdoors, unauthorized services, and other hints of misconfiguration. However by adding a few options we can see more useful data. Let’s explore the other options available to us. With “-a” option then you will get a list of connection and listening ports. This data can be very useful, as you can look at the connection and the listing ports together. However sometimes only the listing ports will be what you need. As you can see below, this system needs to be looked at, there are some unauthorized ports.
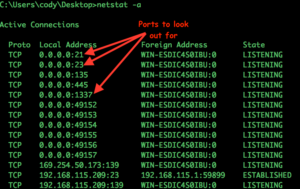
In this example, you can see three interesting ports, 21, 23, & 1337. Each of these ports tell you something about the system but not really very much. For the purpose of this exercise, let’s pretend the only options we have to use is the netstat command, so lets try some more options and see what more we can find out.
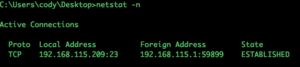
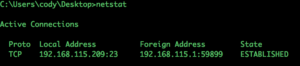
Using netstat with “-n” displays all the options using the number format. This is helpful as the option shows you the IP address on both sides, But the “-n” alone does not seem to provide you enough information. Let’s see if there are other useful options.
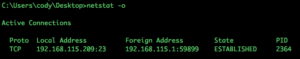
Using netstat with “-o” displays the owning process ID. This is also helpful information, but again like the “-n“, the “-o” does not provide all the information needed. Let’s see of there are other useful options.
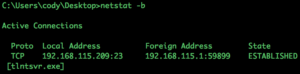
The netstat with the “-b” option displays the executable involved in creating each connection or listening port. This can be extremely helpful, especially when thinking about the Goose and Duck issue. If the port is 80, and some command other than a web server command is shown you can more quickly find the unauthorized service. We can use the “dir” and “find” command together and locate the file running the service.

As you can see in the command, we found two tlntsvr.exe files. You will have to decide which one is the correct file that is running the service, but most of the time the selection is not to difficult. In this case the correct answer is “c:\Windows\System32\tlntsvr.exe“. If you are curious about the other file, the winsxs folder has a special purpose and more information on winsxs can be hound here. Even though the “-b” gave us more good info, we still don’t have all the info we need. Wait, what if we combined all the options together, let’s try that and see what happens.
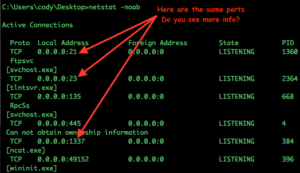
Wow, look at all the great information, we can see an FTP service, a telnet service, and what is that service on port 1337? Hmmm, what is that ncat.exe, could that be a backdoor, we should investigate that more? Let’s try the “dir” and “find” command again.

If we run the command “dir /s/b c:\ | find “ncat.exe”” we can locate the file and look, the file is located in the nmap directory. This file is most definitely a flag, well if this computer was a competition image then this would be a flag. NMAP is a network discovery tool security professionals use all the time to map out a network. NCAT is the NMAP version of a tool called NETCAT, and is a tool used to open sessions to remote computers or to scan open ports and see how the service responds. Both of these tools in the hands of a good guy are not hacking tools, but in the wrong hands, these are most definitely bad tools. In my day job, if I find these tools on a random workstation, I know something bad is going on.
Here are few other links that can he helpful when using netstat and other Windows commands.
- https://www.sans.org/security-resources/sec560/windows_command_line_sheet_v1.pdf
- https://www.sans.org/media/score/checklists/ID-Windows.pdf
- https://www.sans.org/reading-room/whitepapers/incident/simple-windows-batch-scripting-intrusion-discovery-33193
Netstat on Linux
On Linux (Ubuntu) the concepts previously discussed are the same, so I am only going to focus on the differences. There are different options to use in the competition. Listed below are the options I recommend you use.
- -p: display PID/Program name for sockets
- -e: display other/more information
- -a: display all sockets (default: connected)
- -n: don’t resolve names, numeric output only
- -u: provide UDP ports
- -t: provide TCP ports
The Linux version is pretty simple to remember, just think of your favorite peanut butter, see below:
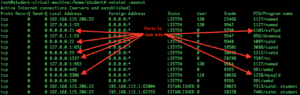
In this example above, you can see many of the interesting services, and there is that 1337 again. The hacker must be all over the place in this network. You can also see the SSH port, mysql, and other ports of interest.
Wrapping Up
These commands are very import to your recon script. I would encourage you to put both of these commands in your recon scripts and pay close attention to flags that are displayed in this output.
