Getting Started with Services
When two computers communicate with one another, one system is the client and the other is the server. Using this simplified definition in today’s environment is not so clean cut. The reason is most workstations or “CLIENT” computers are also servers in some instances. For an example a workstation can have shared file services or the Remote Desktop Services (RDP) and yet we still consider those systems a client. At the same time, as Windows 2008 Server can have a SSH client installed (for example PuTTY) and when connecting to a Linux computer or network device, the Windows 2008 server is a client. The point I am making is this, any device can be a server and a client at the same time. So when evaluating services on a computer for the competitions, we need to understand how to identify services and if that service is authorized and if that services makes the host a server or client.
In this blog post I will discuss Windows 7, Windows 10, and Ubuntu 14 and how to detect the services and if there any server type services enabled. The first step I am going to take is to setup a virtual machine with fresh installations so we can run some commands and get a clear understanding of normal. The hardest part about analyzing services is there are so many services and who really knows what they all mean. A good CyberPatriot should take the time to document services that are normal and then can compare the files with competition images, thereby easily spotting the delta. Once the delta is identified, you would have less research to do.
What is Normal?
As I previously mentioned, trying to understand normal can be a difficult task, but I know you are up to the challenge. The first place we are going to look is at the running services, which can be identified using two methods at the command line. The methods are:
- net start
- This command returns a list of services running in the background. Some of the services are a process needed by the operating system, for example the “DNS Client Service.”
- The DNS Client service is the client component that resolves and caches Domain Name System (DNS) domain names. When the DNS Client service receives a request to resolve a DNS name that is not contained in the local cache, the service queries an assigned DNS server for an IP address for the name.
- On the other hand a service like the server service is used to share files from the host computer and other computers.
- The server service supplies the connections requested by client-side redirectors and provides them with access to the resources they request. The Common Internet File System (CIFS) server service interacts directly with other file-system drivers to satisfy I/O requests, such as reading or writing to a file.
- This command returns a list of services running in the background. Some of the services are a process needed by the operating system, for example the “DNS Client Service.”
- sc query
- Service Console (SC)
- The SC command allows you to fully interact with all the services just as if you where connected via the Services.msc. adding the “query” sub-command tells the system to return all the running services.
Using the Commands
The two commands I showed you have different purposes. For an example the “net start” command is used to start and stop (using the net stop command) services. But when entering the “net start” command you will see a list of services along with the DISPLAY_NAME found with “sc query” command. As with most things in the Windows command line if there is a space in the name you need to include quotes.
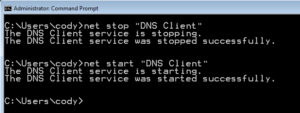
The problem with the “net start” command is there are also services that are disabled. When trying to understand what “NORMAL” is, seeing the disabled services is just as important. In case you are wondering “net stop” does not show the disabled services, but I like the way you are thinking.
The SC Command
The SC command mean the “Service Console”. With this command you can do most anything with the command line as you can with GUI. The idea being is to prep general commands like disabling Telnet, or the IIS service and other steps that could assist in the mitigation of vulnerabilities. Let’s dive into “sc” command a little deeper.
SC Query
The “sc query” provides a list of all services that are running. However, the output of the “sc query” command has much more than the “net start” command. As you can see below there are are two different names, and several other options. We have a similar issue, how do we see the inactive services? However, never fear we can apply a filter.
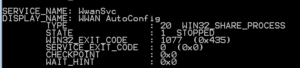
- Disabled Services – sc query state= inactive
- Please note, the space after the “=” is required or the command will fail.
- Enabled Services – sc query
However, we still have one more issue, do we need all the extra data, or can we filter the data down somewhat? Lets use the FIND command in conjunction with SC command. Here are two examples:
- sc query state= inactive | find “_NAME”
- sc query | find “_NAME”
Now we can really filter down the list, but we are not done yet, let’s store the output into a file.
sc query state= inactive | find “_NAME” > output.txt
- sc query – Command used to collect the data in question.
- find – This command looks in the text that “sc query” returns and
Now the output is redirected into a file, and the data can be analyzed much easier.
Windows Versions
The good news is these commands I am showing you will work on all versions of Windows used in the competition. There are other commands we could explore with PowerShell or other 3rd party commands, but as I said before I want to show you commands you can use without installing anything on the target machine.
Comparing Output
Remember to compare the competition image to a known base image, we must first know the base image normal and then show that normal to a output from the competition image. Fortunately Windows has a command called FC, which stands for File Compare. In our case we can use the FC command with no additional arguments.
fc old.txt new.txt
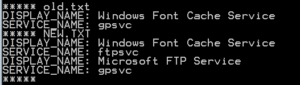
You can see in this example, the “ftpsvc” is found in the new.txt, and therefore helps to narrow down where the possible unauthorized services can be found.
Services with Ubuntu
In Ubuntu we are going to talk about the “service” command. The services are not managed in the same way as windows, but finding the running services is for most part just as easy to do. First we have the “service” command, this is very much like the “sc” command in windows. With the “service” command you can start, stop, restart and other service related functions. You can also run the “service –status-all” and see all the running and configured services.
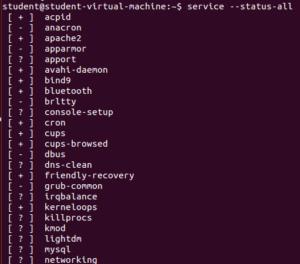
As you can see in the image above, there are some services with a “+“, “–“, and “?“, here is what those designations mean.
- + = running
- – = disabled
- ? = services managed by Upstart.
- Upstart is an event-based replacement for the /sbin/init daemon which handles starting of tasks and services during boot, stopping them during shutdown and supervising them while the system is running.
The trick to this command is how to capture all the output. There are two outputs, the STDERR and STDOUT. When redirecting, the STDOUT will be redirected with “>”, but the STDERR will not be recorded. Here is the run down.
- Redirect stdout to one file and stderr to another file:
- command > out 2>error
- Redirect stderr to stdout (&1), and then redirect stdout to a file:
- command >out 2>&1
- Redirect both to a file:
- command &> out
Here is the full example:
service –status-all &> new.txt
Compare Outputs
In context of CyberPatriots I like to use the “diff -y old.txt new.txt” command. The -y option provides the files side by side and you can easily see the difference.
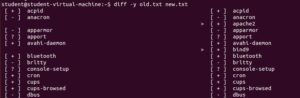
In this example, you can clearly see the new.txt has the apache2 and bind services installed. Whether those are flags or not will depend on the readme file.
Wrapping Up
While these examples are just a few ways to look for services, these examples should start you in to exploring the many other ways to identify flags in the competition.
